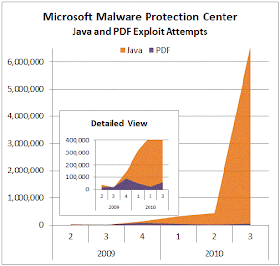
Some others are picking up on something I have been saying for years... "Microsoft reports 'unprecedented wave' of Java malware exploits"
Here is their link:
http://www.zdnet.com/blog/security/microsoft-reports-unprecedented-wave-of-java-malware-exploits/7474?tag=content;search-results-river
And here is their chart to back it up.
Friday, October 29, 2010
Friday, October 22, 2010
Massive web site infections or false positives?
Are there many infected web sites including most twitter shortened links and Alexa.com? Either that or BitDefender is having a lot of false positives?
Wednesday, October 20, 2010
IPCop with Block Out Traffic - BOT
Installing BOT on IPCop is not for the 'faint at heart'. It takes some time because by default it blocks all traffic. Secondly there are easier ways to get it up and running than what they show on their web site. You do not need to create 'groups' you can just add the items to the main screen.
Start by downloading and burning BOT onto a CD and take it to your IPCop computer. Then do the following as seen in the screen shot below:
Download BlockOutTraffic, burn to a CD and put CD into IPcop server.
type 'mount /dev/cdrom'
type 'cd /mnt/cdrom'
type 'cp Block [tab] /'
type 'cd /'
type 'tar zxvf Block [tab]'
type './setup'
When you first go to BOT, it is found under the firewall tab, you need to enter your computers MAC address so that once BOT is running you can override its settings and still access IPcop.
If you have forgotten how to find out what your MAC address here is how to do that, start by right clicking on your network connections;
First you have to create a new rule for each normal service, they are HTTP, HTTPS, POP3, and SMTP. Make sure that you select 'default networks, Green Network' then 'Use Service, Default services', and use the select box to select the service that you are adding, and remember to 'enable' the rule.
once you have your rules enabled then you should see this screen. Now there are some IPcop access rules that need to be added. Mainly they are 'domain' and 'NTP'. It will not work if you add them to the 'Outside' rules as your computers should be getting them from the IPcop server instead of from the outside world.
Last of all you need to add some IPcop rules in the advanced section too. These allow all computers to log into IPcop not just the one that has their MAC address set up in the initial screen.
Start by downloading and burning BOT onto a CD and take it to your IPCop computer. Then do the following as seen in the screen shot below:
BOT Installation
-----------------------Download BlockOutTraffic, burn to a CD and put CD into IPcop server.
type 'mount /dev/cdrom'
type 'cd /mnt/cdrom'
type 'cp Block [tab] /'
type 'cd /'
type 'tar zxvf Block [tab]'
type './setup'
When you first go to BOT, it is found under the firewall tab, you need to enter your computers MAC address so that once BOT is running you can override its settings and still access IPcop.
If you have forgotten how to find out what your MAC address here is how to do that, start by right clicking on your network connections;
First you have to create a new rule for each normal service, they are HTTP, HTTPS, POP3, and SMTP. Make sure that you select 'default networks, Green Network' then 'Use Service, Default services', and use the select box to select the service that you are adding, and remember to 'enable' the rule.
once you have your rules enabled then you should see this screen. Now there are some IPcop access rules that need to be added. Mainly they are 'domain' and 'NTP'. It will not work if you add them to the 'Outside' rules as your computers should be getting them from the IPcop server instead of from the outside world.
Last of all you need to add some IPcop rules in the advanced section too. These allow all computers to log into IPcop not just the one that has their MAC address set up in the initial screen.
Act causing a continuous reset
Sage Act likes to cause computers to continuously reset and restart. There is a simple, quick fix for the problem by using MsConfig in safe mode to disable the "SQl server VSS writer". Now the computer should stop crashing every time it starts.
Then use the ACT uninstall program downloaded from their web site to uninstall ACT. Then you can try reinstalling it again but I make no promises there! I have seen this problem on a fresh clean install of Windows.
Then use the ACT uninstall program downloaded from their web site to uninstall ACT. Then you can try reinstalling it again but I make no promises there! I have seen this problem on a fresh clean install of Windows.
Monday, October 18, 2010
UDP Port 8881 Virus - A BitDefender 2011 problem
UPDATE: This is a BitDefender 2011 problem - Disable P2P file sharing in the Bitdefender 'updates' section to fix it. This is shocking and appalling that Bitdefender would open a hole in the firewall and allow almost anyone access to your computer!
I am still fighting the UDP Port 8881 virus that appears to come from visiting a Twitter account. So far I can tell that IPCop logs about 6000 blocked UDP port requests inbound to the infected computer every day. The infected computer according to WireShark, just goes out to random web pages and downloads pictures. That appears to then trigger the port 8881 responses back towards the infected computer. Reformatting the hard drive does NOT get rid of the virus. I assume that the virus comes back when you copy back 'my documents' but I am not even sure of that. However NO ANTI VIRUS program can detect this virus after a week of fighting it.
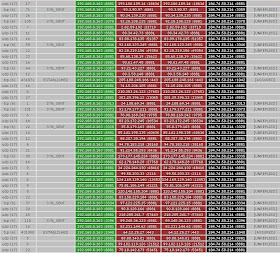
Here are some WireShark screen pictures. First is the incoming traffic to the infected computer. This one is kind of funny. It says "go away we're not home". Click on the image to see it full size.
Here is a typical IPCop screen showing the connections opened by the virus;
I am still fighting the UDP Port 8881 virus that appears to come from visiting a Twitter account. So far I can tell that IPCop logs about 6000 blocked UDP port requests inbound to the infected computer every day. The infected computer according to WireShark, just goes out to random web pages and downloads pictures. That appears to then trigger the port 8881 responses back towards the infected computer. Reformatting the hard drive does NOT get rid of the virus. I assume that the virus comes back when you copy back 'my documents' but I am not even sure of that. However NO ANTI VIRUS program can detect this virus after a week of fighting it.
Here are some WireShark screen pictures. First is the incoming traffic to the infected computer. This one is kind of funny. It says "go away we're not home". Click on the image to see it full size.
Here is a typical IPCop screen showing the connections opened by the virus;
Thursday, October 14, 2010
Rear Projection Setup
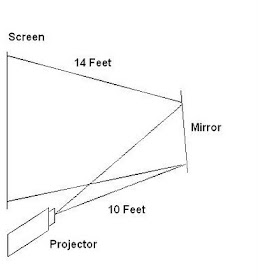
I have seen a church allot 30 feet behind the projection screen for a rear projection setup. this is unnecessary all you need is a mirror. There are two setups that can be used, project from below up to the mirror and from just below the screen at the mirror. The setups are diagrammed below:
Projector located below the mirror.
Projector located just behind the screen.
Now about the screen. As you may know a glass bead screen is by far the best screen. After that a white sheet also works. In forward projection setups you can use reflective white paint or regular white paint as well.
Projector located below the mirror.
Projector located just behind the screen.
Now about the screen. As you may know a glass bead screen is by far the best screen. After that a white sheet also works. In forward projection setups you can use reflective white paint or regular white paint as well.
IPCop Revisited once again...
There are ongoing problems with Snort IDS not updating on IPCop. So I thought I would try out Smoothwall instead. Smoothwall installed much faster and easier than IPcop. There were almost no questions that required a lot of technical knowledge. then menus in Smoothwall are arranged differently and took a little getting used to. Then the problems started. I could not even get IDS to turn on in Smoothwall. I have been watching a virus infected computer trying to ensure that the virus had been completely removed and so having no IDS was simply not an option.
Also when I enable the email virus filter it blocked ALL of my email as containing a virus. This was not
acceptable either, so although Smoothwall is much easier to install it is not as usable as IPCop, and will not be
used by me at this point.
Here is a simple diagram on how IP cop is setup up as an Internet server and a firewall.
I thought I would include some IPCop configuration screens so you can see how they should look. Notice that I do nut use VPN, I do not like to put a hole through my firewall unless the boss absolutely demands it!
Most of the time you will want DNS to be set up and running. Sometimes you have a file server that does the DNS thing instead.
Then there is the Web proxy server. This is needed in order to log who is accessing what. It also speeds up the Internet a little by serving some pages from its cache.
Next is enabling the time server. This helps to keep all of your computers synchronized to the same time.
Some say that enabling IDS on Red is just a waste of time because it only tells you that you are under attack, but that is a given being connected to the Internet. However it has been telling me that someone out there is trying to access the formerly infected computer, so IMO it is very useful!
I do not know if configuring a static DNS is necessary, and if so what one do you use?
Also when I enable the email virus filter it blocked ALL of my email as containing a virus. This was not
acceptable either, so although Smoothwall is much easier to install it is not as usable as IPCop, and will not be
used by me at this point.
Here is a simple diagram on how IP cop is setup up as an Internet server and a firewall.
I thought I would include some IPCop configuration screens so you can see how they should look. Notice that I do nut use VPN, I do not like to put a hole through my firewall unless the boss absolutely demands it!
Most of the time you will want DNS to be set up and running. Sometimes you have a file server that does the DNS thing instead.
Then there is the Web proxy server. This is needed in order to log who is accessing what. It also speeds up the Internet a little by serving some pages from its cache.
Next is enabling the time server. This helps to keep all of your computers synchronized to the same time.
Some say that enabling IDS on Red is just a waste of time because it only tells you that you are under attack, but that is a given being connected to the Internet. However it has been telling me that someone out there is trying to access the formerly infected computer, so IMO it is very useful!
I do not know if configuring a static DNS is necessary, and if so what one do you use?
Wednesday, October 13, 2010
New Virus Infection
There are a lot of fake, virus infected, Linkedin emails going around. Supposedly this virus might have come from just viewing a profile on the web site or possibly on Twitter? The first symptom was that McAfee was popping up every 10 seconds with a message saying that it had blocked a virus. Then McAfee went down all together and the virus took over. Alt+Control+Delete did not work. I could download Malwarebytes but it would not run.
I now know that Symantec has a Trojan.Vundo removal tool that likely would have fixed this problem. Instead I used Start, Run, and MsConfig to shut down almost all of the Startup items. Then I downloaded Malwarebytes and ran it again. This time it ran but would not update. There is an alternate program killing program called Rkill.com that would have solved that problem. However Malwarebytes did remove some infections and after the computer was restarted it was able to successfully update and remove the rest of the infections.
The infection got through by using a Java Script. If the user had been running FireFox with NoScript they would have never had the problem. I will not digress to ranting about how Java should be banned as over 80% of virus are using java to trash millions of computers........
This virus keeps coming back, even after reformatting the hard drive and reinstalling Windows from CD's. It could be when email is imported or when my documents are copied? The symptoms are repeated IPCop firewall reports of "ICMP Destination Unreachable Communication Administratively Prohibited" when someone tries to directly access the computer from the outside world and lots of traffic on port 8881. Every now and then the computer tries to open 20 or 30 UDP connections to port 8881 and some other other ports like 1889, 1814, 1850, 1855, and 1877 among others.
Malwarebytes has removed a dozen virus' and BitDefender keeps finding some too. But it keeps coming back! I hate that when reformatting the hard drive does not get rid of it. There will be more information coming as soon as I can figure it out. The UDP on Port 8881 has to be a key to the problem?
I now know that Symantec has a Trojan.Vundo removal tool that likely would have fixed this problem. Instead I used Start, Run, and MsConfig to shut down almost all of the Startup items. Then I downloaded Malwarebytes and ran it again. This time it ran but would not update. There is an alternate program killing program called Rkill.com that would have solved that problem. However Malwarebytes did remove some infections and after the computer was restarted it was able to successfully update and remove the rest of the infections.
The infection got through by using a Java Script. If the user had been running FireFox with NoScript they would have never had the problem. I will not digress to ranting about how Java should be banned as over 80% of virus are using java to trash millions of computers........
This virus keeps coming back, even after reformatting the hard drive and reinstalling Windows from CD's. It could be when email is imported or when my documents are copied? The symptoms are repeated IPCop firewall reports of "ICMP Destination Unreachable Communication Administratively Prohibited" when someone tries to directly access the computer from the outside world and lots of traffic on port 8881. Every now and then the computer tries to open 20 or 30 UDP connections to port 8881 and some other other ports like 1889, 1814, 1850, 1855, and 1877 among others.
Malwarebytes has removed a dozen virus' and BitDefender keeps finding some too. But it keeps coming back! I hate that when reformatting the hard drive does not get rid of it. There will be more information coming as soon as I can figure it out. The UDP on Port 8881 has to be a key to the problem?
Monday, October 11, 2010
Free Instant Keyword Analyzer Tool
Google no longer pays any attention to the 'keywords' meta tag on your web site. Instead they do an analysis of your web site to find out what are the actual keywords that are really used. So I tried to find out what were our actual keywords on our web site. It turns out that there are web sites that will do that for you but they require that you enter your phone number and an email address so they can annoy you with salesmen calling and emailing you.
I thought that I could easily write a program to do the job so I have started developing 'KAT' or "Keyword Analyzer Tool". It is totally FREE and gives the results in seconds! It will strip the HTML code from your web site, feed that into an array and then count the number of times each word is used. I hope to add the ability to also count those words in links, headings, and in strong soon.
Keyword Analyzer Tool
I thought that I could easily write a program to do the job so I have started developing 'KAT' or "Keyword Analyzer Tool". It is totally FREE and gives the results in seconds! It will strip the HTML code from your web site, feed that into an array and then count the number of times each word is used. I hope to add the ability to also count those words in links, headings, and in strong soon.
Keyword Analyzer Tool
Tuesday, October 5, 2010
Hawking WIFI Antenna
I recently purchased a Hawking Antenna. It was really cheap because it rattled. That was because the antenna mount was slightly broken and it was easily fixed with some glue.
Anyway the antenna is actually an ordinary antenna with a metal reflector. I will give the measurements shortly. Basically you can easily make it yourself. If you carefully pull the top end off you can then see how it works. Hopefully I will be able to do some comparison tests too.
The metal shield/Reflector is about 1.25 inches from the center of the antenna. In my tests this antenna combined with an EDUP USB wireless card detected twice as many wireless networks in our area compared to the built in wireless adapter in my notebook computer.
Anyway the antenna is actually an ordinary antenna with a metal reflector. I will give the measurements shortly. Basically you can easily make it yourself. If you carefully pull the top end off you can then see how it works. Hopefully I will be able to do some comparison tests too.
The metal shield/Reflector is about 1.25 inches from the center of the antenna. In my tests this antenna combined with an EDUP USB wireless card detected twice as many wireless networks in our area compared to the built in wireless adapter in my notebook computer.
Friday, October 1, 2010
EDUP USB wireless adapter drivers
I recently purchased one of these tiny EDUP wireless adapters on EBay. First of all they advertise them as 'high power' but they are really not 'high power' if you were expecting 500 MW or 1000 MW like the real high power USB adapters can put out. If you really want high power add 500, 1000, or even 2000 MW to your search in EBay. On the other hand the external antenna may double your range compared to the antenna that is built into most laptops.
Anyway I lost the driver disk and could not find it. I Googled it but no one seemed to know where to find the driver! When you plug it in the computer says something about a RTL 8188 driver and that is the secret. Just go to www.Realtek.com and search for the 8188SU driver.
Here is a link but you may have to cut and paste it into your browser:
http://www.realtek.com/search/default.aspx?keyword=rtl8188su
Anyway I lost the driver disk and could not find it. I Googled it but no one seemed to know where to find the driver! When you plug it in the computer says something about a RTL 8188 driver and that is the secret. Just go to www.Realtek.com and search for the 8188SU driver.
Here is a link but you may have to cut and paste it into your browser:
http://www.realtek.com/search/default.aspx?keyword=rtl8188su